Introduction
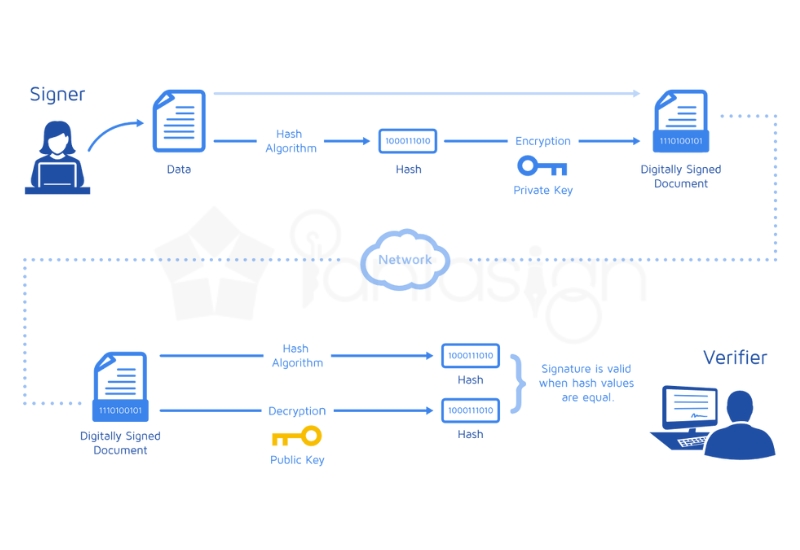
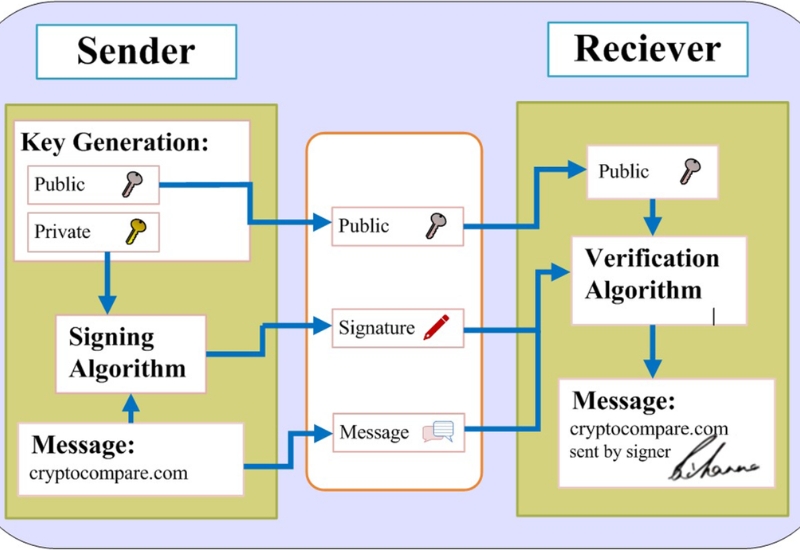
As digital transactions become more common, the security of digital signatures is a top priority for individuals and businesses. Digital signatures ensure the authenticity and integrity of documents, but if not properly protected, they can be vulnerable to misuse or fraud.
By implementing strong security measures, users can safeguard their digital signatures against unauthorized access and potential cyber threats. This article provides essential tips to enhance the security of digital signatures and ensure safe online transactions.
Use Strong Authentication Methods
A strong authentication process is the first line of defense in securing digital signatures.
Best Practices for Authentication Security
- Use multi-factor authentication (MFA) to add an extra layer of protection.
- Choose a provider that offers biometric authentication, such as fingerprint or facial recognition.
- Ensure that passwords used for digital signature access are strong and unique.
- Multi-factor authentication makes it difficult for attackers to gain unauthorized access, reducing the risk of misuse.
Protect Your Private Key
The security of a digital signature depends on the confidentiality of the private key used to generate it.
Ways to Keep Your Private Key Secure
- Store the private key in a hardware security module (HSM) or a secure token.
- Avoid sharing or storing private keys in unprotected locations, such as emails or personal devices.
- Use encryption to protect private key files from unauthorized access.
- Without proper private key protection, a digital signature can be compromised, leading to potential fraud or identity theft.
Use a Trusted Digital Signature Provider
Selecting a reliable and compliant Certifying Authority (CA) ensures the security and validity of digital signatures.
What to Look for in a Digital Signature Provider
◆ Compliance with industry standards such as eIDAS, CCA, or global PKI frameworks.
◆ Use of secure encryption algorithms for data protection.
◆ Regular security audits and compliance checks to prevent vulnerabilities.
Choosing a reputable digital signature provider minimizes security risks and ensures legal validity.
Enable Document Encryption
Encrypting digitally signed documents adds another level of security by preventing unauthorized access or tampering.
Best Practices for Document Encryption
◆ Use end-to-end encryption to protect sensitive documents during transmission.
◆ Apply password protection on signed files to restrict unauthorized viewing.
◆ Choose encryption standards such as AES-256 for maximum security.
Encryption ensures that even if a document is intercepted, it cannot be accessed without the proper decryption key.
Regularly Update Software and Security Measures
Keeping digital signature software and security protocols up to date helps protect against new threats.
Security Updates to Implement
◆ Install updates for digital signature applications and security tools regularly.
◆ Use antivirus and firewall protections to prevent malware attacks.
◆ Regularly monitor for unauthorized access attempts to digital signature systems.
Outdated software can create vulnerabilities, making it easier for attackers to exploit security gaps.
Verify Signed Documents Before Accepting
Businesses and individuals should always verify digital signatures to ensure authenticity before accepting signed documents.
Steps for Verifying Digital Signatures
◆ Check the certificate validity and issuer details.
◆ Ensure the signature has not been revoked or expired.
◆ Confirm the document integrity by comparing the original file with the signed version.
Verifying signatures before accepting documents helps prevent fraudulent transactions.
Be Cautious of Phishing Attacks and Social Engineering
Cybercriminals often use phishing attacks to steal digital signature credentials.
How to Avoid Phishing Scams
◆ Never click on suspicious links or download attachments from unknown sources.
◆ Verify the sender’s identity before responding to requests for digital signature information.
◆ Use email filtering and anti-phishing tools to detect malicious emails.
Staying vigilant against phishing attempts can prevent unauthorized access to digital signatures.
Monitor and Audit Digital Signature Usage
Regularly reviewing digital signature usage helps identify suspicious activities before they become security threats.
Monitoring and Audit Practices
◆ Keep detailed logs of all signed transactions for auditing purposes.
◆ Set up alerts for unusual signing activity, such as multiple sign-in attempts.
◆ Conduct periodic security reviews to assess vulnerabilities and strengthen security measures.
By monitoring digital signature usage, businesses can quickly detect and respond to potential threats.
Securing a digital signature requires a combination of strong authentication, encryption, regular software updates, and vigilance against cyber threats. By following these best practices, individuals and businesses can protect their digital signatures from unauthorized use and ensure safe digital transactions.
At Pantasign, we prioritize security by providing trusted and legally compliant Digital Signature Certificates (DSCs) with industry-leading encryption and authentication measures.
Get a secure digital signature today with Pantasign.
Powered by Froala Editor